Security Testing Strategies for Robust Applications
Introduction
In today’s hyper-connected digital landscape, where technology rapidly evolves, security testing has become an essential part of software development. Businesses and individuals rely on applications for various purposes, making it crucial to protect sensitive data and systems from security threats.
Additionally, Application Programming Interfaces (APIs) play a key role in data exchange and functionality across applications. However, ensuring API security is just as important as their convenience. Strengthening APIs against vulnerabilities is a critical step in securing digital assets.
Understanding Security Testing
It is a systematic process that identifies weaknesses in software applications and evaluates their susceptibility to security risks. The primary objective is to uncover vulnerabilities in security controls that attackers might exploit, potentially compromising data confidentiality, integrity, or availability.
Why It Is Essential?
1. Protecting Sensitive Data: With personal, financial, and business information stored digitally, security breaches can cause serious damage. Security testing ensures confidentiality and prevents unauthorized access.
2. Maintaining User Trust: Users expect secure handling of their data. A breach can damage reputation and erode customer confidence. Security testing demonstrates a commitment to data protection.
3. Regulatory Compliance: Laws like GDPR and HIPAA enforce strict data security regulations. Security testing ensures compliance and prevents legal penalties.
4. Cost Efficiency: Detecting and fixing vulnerabilities early in development is far less expensive than addressing security incidents after a breach.
5. Ensuring Business Continuity: Cyberattacks can disrupt operations. Security testing reduces the risk of downtime, keeping businesses functional.
Best Practices for API Security
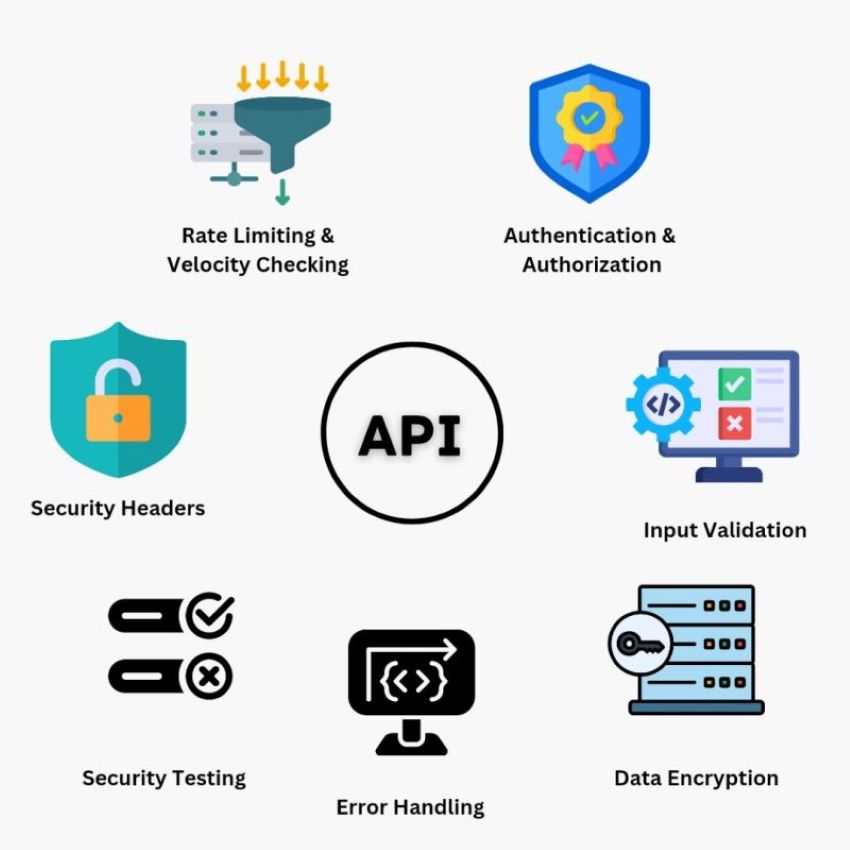
It is crucial to prevent unauthorized access and cyber threats. Here are some top API security best practices to safeguard digital assets:
– Authentication & Authorization: Use OAuth, API keys, or token-based authentication to ensure only authorized users can access APIs.
– Rate Limiting: Prevent abuse and maintain performance by setting API request limits.
– Data Encryption: Encrypt API data using TLS/SSL to protect it from interception.
– Input Validation: Sanitize user inputs to prevent injection attacks like SQL injection and XSS.
– Security Headers: Use HTTP security headers such as Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS) to enhance security.
– Error Handling: Avoid exposing sensitive system details in error messages to prevent data leaks.
– Security Testing: Regular security assessments, penetration testing, and code reviews help identify and fix vulnerabilities.
Key Principles
1. Comprehensive Coverage: Security testing should encompass all facets of an application, including authentication, authorization, input validation, session management, and data protection.
2. Realistic Testing: Test scenarios should closely resemble real-world attack scenarios to unveil vulnerabilities that malicious actors might exploit.
3. Continuous Enhancement: It should be an ongoing process, spanning the software development lifecycle from design and development to deployment and maintenance.
4. Interdisciplinary Collaboration: Effective resolution of security issues necessitates collaboration between development, operations, and security teams.
Methodologies and Best Practices
Different approaches help ensure robust security testing. Some of the most effective methodologies include:
1. Penetration Testing
Ethical hackers simulate cyberattacks to identify vulnerabilities and assess the system’s ability to withstand them.
2. Static Application Security Testing (SAST)
SAST analyzes source code for security flaws, helping detect vulnerabilities early in development.
3. Dynamic Application Security Testing (DAST)
DAST scans a running application to identify real-time security risks.
4. Security Code Reviews
Manual reviews by security experts help detect vulnerabilities that automated tools might miss.
5. Security Training
Training development and testing teams in best security practices prevents security lapses.
6. Vulnerability Management
A structured approach to tracking and resolving vulnerabilities ensures timely remediation.
In Conclusion
Security testing is an essential part of software development, acting as a safeguard against evolving cybersecurity threats. By adopting application and platform security measures and integrating robust security testing strategies, businesses can protect sensitive data, maintain user trust, and strengthen their digital infrastructure. In today’s interconnected world, investing in security testing is not optional—it’s a necessity for long-term success.
Do you like to read more educational content? Read our blogs at Cloudastra Technologies or contact us for business enquiry at Cloudastra Contact Us.
