Why Cloud Enterprise Security Provider Matters

Today, cloud computing is leading the journey. All sizes of businesses are working on their applications, files, and customer data to the cloud. These changes offer many advantages like flexibility, cost savings, speed, and scalability. However, it also comes with some risks. Also cyberattacks are growing. Data leaks, ransomware, and insider threats are increasing in cloud systems.
And that’s why cloud security is not just a tech issue but also it’s a business survival issue. You should protect your data and systems in this separated, cloud enterprise security provider. Whether you’re a startup or a big company, cloud security should be the first priority.
Fortunately, you won’t have to do it alone. Cloud enterprise security providers give amazing tools and expertise to help to keep your data safe. But you also need to understand the best practices, tools, and people like your DevOps engineers who can keep everything working securely behind the scenes.
In this blog, we’ll talk about the cloud security essentials that every business needs to know. We’ll explore common threats, smart strategies, and how to build a secure cloud enterprise security provider and technologies.
Understanding Cloud Security in a Distributed World
The cloud is a huge space. Unlike traditional IT environments where everything was hosted on-premise, cloud systems store data across different servers and locations and sometimes even across countries. This flexibility is good for performance and uptime, but it also opens doors for certain challenges.
Your data might move between applications, data centers, and cloud regions. Devices from around the world may access your systems 24/7. This distributed nature makes data protection more complex. Without the right security layers in place, your business could be vulnerable to easy access, data leaks, or service disruptions.
You need a strong cloud security foundation built on visibility in such a world to control, and continuous monitoring.
Who Are Cloud Enterprise Security Providers?
Cloud enterprise security providers are companies that specialize in protecting cloud environments. They provide tools, services, and expertise to help businesses manage risks, detect threats, and respond to incidents.
These providers work closely with public cloud platforms like AWS, Microsoft Azure, Google Cloud, and private or hybrid environments. Some known cloud security providers include Palo Alto Networks, CrowdStrike, Trend Micro, and Zscaler.
Their offer features that have:
– Threat detection and protection
– Cloud firewalls and virtual private networks
– Identity and access management (IAM)
– Encryption services
– Compliance monitoring
– Security services management
By collaborating with a trusted provider, businesses get access to advanced technology and professional guidance. This makes it easier for the business to stay ahead in evolving cyber threats.
Common Threats in the Cloud
Cloud environments face a huge range of threats. Understanding them beforehand and preparing your defenses is important.
1. Misconfigured Cloud Settings:
This is one of the most common reasons for cloud data breaches. Small mistakes like leaving a storage bucket open to the public can leak sensitive data.
2. Weak Identity and Access Controls:
If users have many privileges or poor passwords, attackers can easily access their accounts.
3. Insecure APIs and Applications:
Cloud enterprise security providers depend on APIs for communication. If not protected properly, they can become entry points for hackers.
4. Insider Threats:
Sometimes, employees or contractors accidentally cause data leaks or damage to the organization.
5. Malware and Ransomware Attacks:
Just like on traditional systems, cloud enterprise security providers can also be targeted by malicious software.
Clearly, cloud security must be proactive and cover all these threat areas.
Cloud Security Best Practices Every Business Should Follow
To protect your data in the cloud, you need to follow some proven cloud security best practices. Let’s explore them in detail.
1. Enable Strong Identity and Access Management (IAM)
Only giving access to those who need it. Use role-based access control (RBAC) to assign specific access. Make sure to enable multi-factor authentication (MFA) for every account. These simple steps can stop most unknown logins.
2. Use Data Encryption in Cloud
Data encryption in cloud enterprise security providers are very important. Encrypt your data both at rest (when stored) and in transit (when moving between systems). Many cloud enterprise security providers give built-in encryption tools and key management services to make this simpler.
3. Monitor Everything Continuously
Visibility is the key in cloud security. Use tools to log and monitor user activity to file access, and traffic patterns. Set up alerts for unusual activity. The sooner you detect a problem, the faster you can fix it.
4. Automate Security Checks
Manual security tasks can’t work with fast-changing cloud systems. That’s why automation is complex. For example, your DevOps engineers can use automated scripts to check for open ports, open databases, or outdated software versions. Regular security testing helps to catch issues before attackers do.
5. Perform Regular Security Audits
Security is not a one-time work. You should make this a part of your business routine. Schedule regular security reviews, penetration testing, and audits. Cloud computing managed services providers help to run these assessments and give you insights into what needs improvement.
The Role of DevOps Engineers in Cloud Security
In modern cloud environments, DevOps engineers play an important role in building and maintaining systems. They work at the intersection of software development and IT operations, and their actions directly impact cloud enterprise security providers.
And here’s how they work:
– Infrastructure as Code (IaC): DevOps engineers use code to set up a cloud environment. This checks that every environment is built securely and consistently.
– CI/CD Pipelines: Security can be built into automated pipelines to check that code is scanned for vulnerabilities before use.
– Patch Management: DevOps teams can quickly update systems to fix known security bugs.
– Monitoring and Incident Response: They set up monitoring tools and help in responding to threats when detected.
By integrating security into DevOps processes (often called DevSecOps), businesses can enhance their cloud security without slowing down the progress.
Cloud Computing Managed Services and Their Security Role
Many businesses use cloud computing managed services to manage their infrastructure, storage, networking, and databases. These services allow companies to focus on their main work while the provider sees the backend works.
However, security is a shared responsibility. While the service provider handles the security of the cloud (such as physical data centers and platform security), the business is responsible for security in the cloud meaning user access, data encryption, app configuration, and so on.
Working with managed service providers that can also offer security solutions can help in filling this gap. They can check that best practices are followed, and your environment is secure as it grows.
Compliance and Regulations in the Cloud
Many industries have strict rules about how their data is stored and handled. These include regulations like:
– GDPR (Europe)
– HIPAA (Healthcare, US)
– PCI-DSS (Payment data)
– ISO 27001 (Information security standard)
If you are failing to meet these standards- it can lead to fines or loss of customer trust. Fortunately, top cloud enterprise security providers offer tools that help with compliance. These tools automatically track data handling, access control, and incident response steps to prove compliance during audits.
Staying compliant is not just a legal issue but also it’s a trust issue. Customers want to know whether their data is in safe hands or not.
Building a Culture of Cloud Security
Only tools and providers can’t secure your cloud. People and processes are also important. And that’s why it’s important to build a security-first culture in your organization.
Teach your employees about phishing attacks, secure password habits, and how to report suspicious activity regularly. Encourage your DevOps engineers to add security in every step of development. And empower your IT team to work closely with your cloud security partners.
When everyone plays their role in protecting data, your cloud environment becomes much safer.
Choosing the Right Cloud Enterprise Security Provider
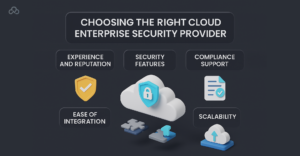
Choosing the right cloud enterprise security provider can feel overwhelming with so many vendors out there. So, here is the thing you should look for?
– Experience and Reputation: Choose a provider with expertise in your industry.
– Security Features: Look for advanced threat detection, data loss prevention, IAM, and encryption support.
– Compliance Support: Check that they help with regulatory requirements which are relevant to your business.
– Ease of Integration: The solution should fit easily into your current tech stack.
– Scalability: As your business grows, your security should also grow with it.
Take your time to evaluate options. A good partner can save you from huge losses in the future.
Conclusion
In today’s world, cloud security is more important than ever. With data moving across platforms, devices, and locations, businesses must take proactive steps to protect them no matter what. That means using encryption, enforcing access controls, monitoring threats, and working closely with cloud enterprise security providers.
It also means involving the right people especially DevOps engineers who can add security into your systems from the first day. And don’t forget to work on cloud computing managed services to grow securely.
By following cloud security best practices and training your teams, and choosing the right partners, you can protect your business, your customers, and your future.
Start today. Because in the cloud, security is not just a feature but it’s a responsibility.
Do you like to read more educational content? Read our blogs at Cloudastra Technologies or contact us for business enquiry at Cloudastra Contact Us